🔑 4 methods for API authentication
If you're building integrations you'll need to authenticate your APIs. This post covers 4 popular methods to do so!
Hey friends ✨,
In today's issue, we're diving into API authentication!
It’s the process of verifying the identity of a user and it’s crucial to ensure only the right people access certain data.
Let's jump in ⬇️
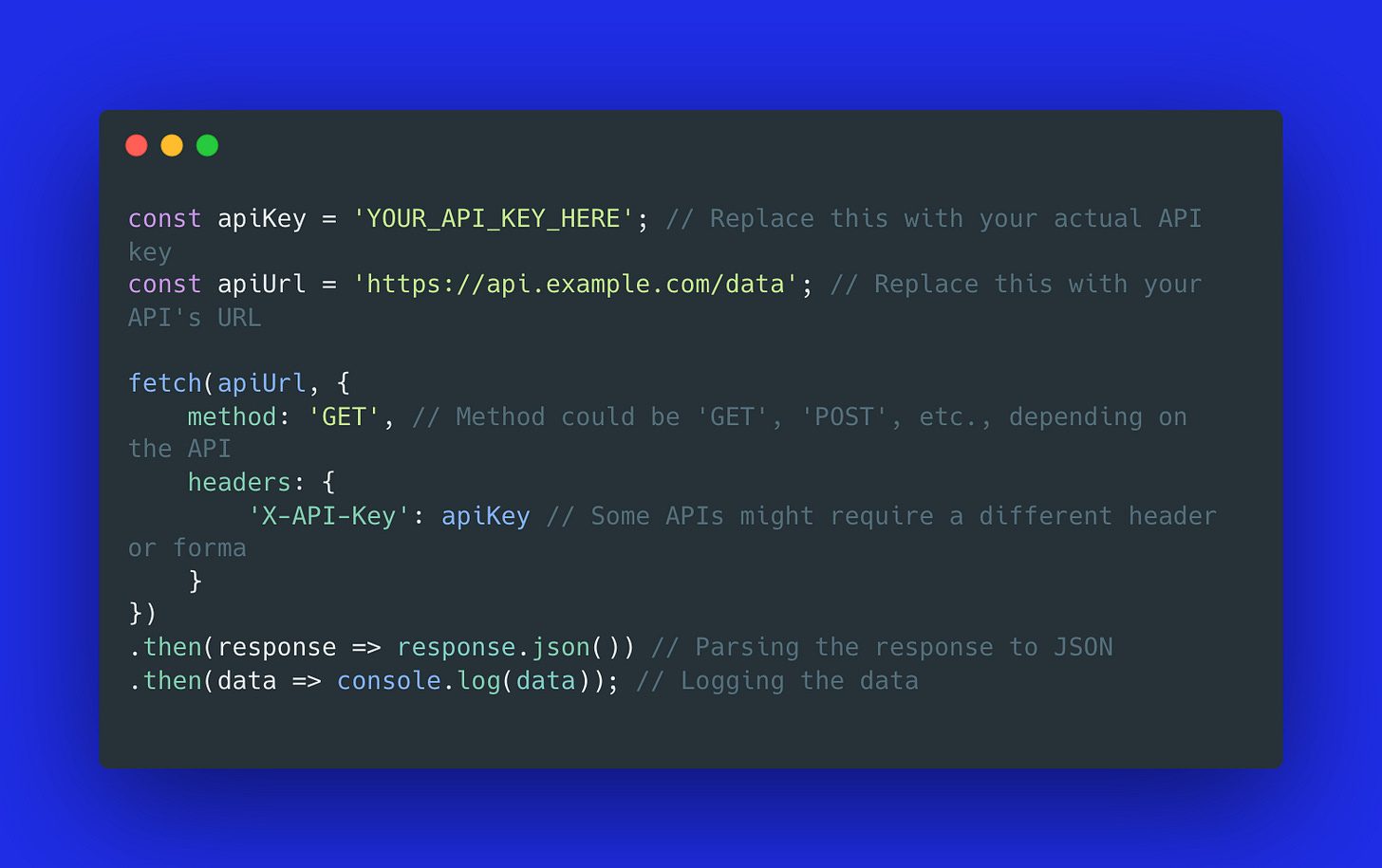
1. API key
An API key is like a secret password. Each user or app gets its own unique key. This key must be included in every request to the API.
It works by including this key in every API request to validate access.
It's best for services where basic access control is needed without the complexity of user-level security.
Examples:
Google Maps API: Developers use API keys to authenticate requests for Google Maps services, allowing them to embed Google Maps on web pages and retrieve location data.
SendGrid: An email delivery service that uses API keys to authenticate requests for sending emails through its API.
2. OAuth
OAuth allows users to grant apps limited access to their data without sharing their passwords.
It works by authorizing token-based access to user data from other services, with OAuth 2.0 being the most widely adopted version.
It’s best for apps that need to interact with user data from other platforms, like social media integrations.
Examples:
Twitter: Uses oAuth so third-party applications can access user data or perform actions on behalf of users without exposing user passwords.
Spotify: Uses OAuth to let third-party apps access user information and playlists,
3. Basic auth
Basic auth is a simple username and password verification method.
It works by sending credentials (username + password) with each request. It’s usually encoded but not encrypted, making it less secure but easy to implement.
It’s best for internal services or scenarios where data sensitivity is low.
Examples:
This approach is largely obsolete in public services; for instance, Microsoft discontinued its use in Exchange Online last August. But you might still encounter it in older or proprietary software applications.
4. JSON Web Tokens (JWT)
JWTs are like secure, secret notes that carry user information.
It works by issuing tokens after successful authentication. This token holds user info in a small, easy-to-check way.
It’s best for single-page applications (SPAs) and mobile apps that require updates without reloading pages.
Examples:
Auth0: Uses JWTs for securing API calls and managing user sessions.
Firebase Authentication: Uses JWTs for managing user sessions and identifying users across various Firebase services.
And that’s it! These are 4 popular ways to authenticate APIs
Which is your favorite?
Lola